Generate Aes 256 Key Online
Encryption provides one of the best methods for securing digital data. Encryption allows the user to obfuscate data through a code that can only be decrypted by the user or other trusted individuals. LastPass simplifies your digital life. From your LastPass vault, you can store passwords and logins, create online shopping profiles, generate strong passwor.
- Aes 256 Software
- Generate Aes 256 Key Online Login
- Generate Aes 256 Key Online Test
- Generate Aes 256 Key Online Generator
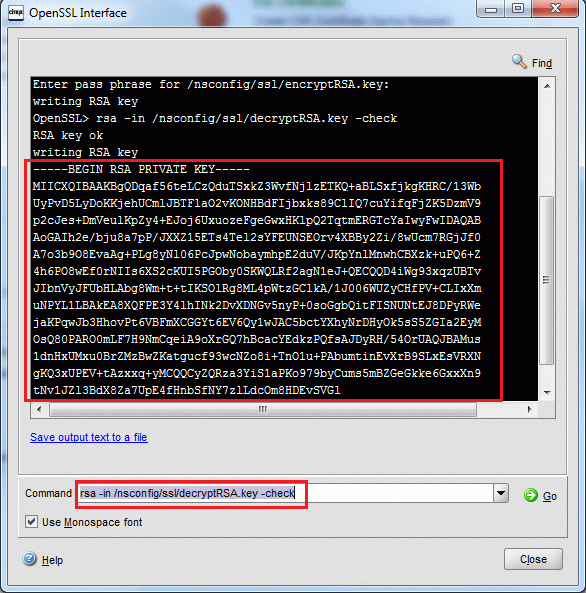
Ssh provides secure access to the remote system. The traffic between systems are encrypted using encryption algorithms. There are different encryption algorithms. RSA is the most popular asymmetric encryption algorithm. In this tutorial we will look how to create RSA keys with ssh-keygen
RSA algorithm is created by researchers named Ron Rivest, Adi Shamir and Leonard Adleman in the MIT. And named with their names first letters. It is asymmetric or public encryption algorithm provides a lot of flexibility. We can generate different size of keys with RSA. RSA is used to make secure SSH, OpenGP, S/MIME, SSL/TLS etc.
Actually ssh-keygen will create RSA keys by default. So we do not have to specify the algorithm but in order to be sure and provide information we can explicitly specify the RSA key creation. We will use -t option in order to specify the RSA algorithm.
By default RSA key is generated into user home directory ~/.ssh/id_rsa . We can change this default directory during the generation or by providing the path as parameter. We will use -f option in order to change path and file name. We will create key named test in to the current working directory.
There will be two files named;
testis the private keytest.pubis the public key
“To acquire knowledge, one must study;
but to acquire wisdom, one must observe.”
― Marilyn Vos Savant
Aes 256 Software
Contents

- Conclusion
1. Introduction
We have previously covered using RSA for file encryption in java. We have also covered in a separate article the process of generating a digital signature for a file and verification using RSA. Let us now combine the two and develop a procedure for encrypting a file and generating a digital signature for exchange between two parties.
When two parties want to securely exchange messages, we use digital signature in addition to encryption to assure the receiver that the message came from the sender, and has not been tampered in transit. Thus, the encryption provides privacy, and the digital signature provides authentication.

Let us assume that party A wants to send party B a secure message. The process works as follows: A generates an AES secret key and encrypts the key using B’s public key. A now uses the AES secret key to encrypt the actual message to be sent. Finally, A generates a digital signature (using A’s private key) for the message. All these components are packed into a single file in the following order: the encrypted AES key, followed by the initialization vector, the encrypted message and finally by the digital signature.
Generate Aes 256 Key Online Login
When this message is sent to B, B can decrypt the message and be assured it came from A only as follows: B decrypts the AES secret key using his own private key, reads the IV and decrypts the message using the AES secret key, and finally verifies the digital signature of the decrypted message by using A’s public key.
Let us see how this is implemented in code.
2. Java Imports
The following java imports are required.

3. Load or Generate the RSA Public and Private Keys
First and foremost, both A and B need to generate RSA public and private key pairs and save them as follows.
A and B exchange the public keys so A has B’s public key, and vice versa.
Load the public and private keys from file as follows:
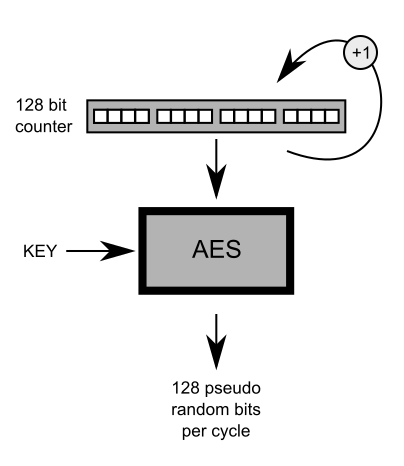
4. Generate the AES Encryption Key
The AES secret key and the initialization vector is generated as follows:
5. Encrypt and Save the AES Encryption Key
The first part of the output file contains the AES encryption key encrypted using B’s public key, followed by the initialization vector. It is saved as follows:
6. Encrypt the Message and Sign it
Generate Aes 256 Key Online Test
Next step is to encrypt the actual message using the AES secret key, and sign the message using A’s public key.
The static method signFile() is defined as follows. It accepts a Cipher object to encrypt the file, a Signature object to sign the message, and an InputStream and OutputStream to read the message from and write the output.
The output file is now ready. Send it to B via any means – the communication channel need not be secure.
7. Decrypting the AES Key
Now that the file has been received by B, decrypting it is next.
First step is to compute the length of the encrypted message. Since the output file consists of the encrypted AES key, the initialization vector and the 256 byte signature at the end, the length of the encrypted message is:
Note that this length may be different from the length of the unencrypted message since encryption proceeds by blocks.
Now B can use his private key to decrypt the AES secret key included in the file.
8. Loading the Initialization Vector
Loading the initialization vector (IV) is next.
Generate Aes 256 Key Online Generator
9. Decrypting the Message and Verifying the Signature
Verifying the signature requires A’s public key. This assures B that A has indeed sent the message.
Decryption of the message is done using the AES secret key.
The static method authFile() is shown below. It decrypts the message update dataLen and verifies the signature of the decrypted message.
Conclusion
In this article, we saw how to encrypt a file for a receiver and also sign it so the receiver is sure it came from us. It involves generating an AES key, using that AES key for encryption and encrypting the AES key using receiver’s public key. The receiver can then unlock the AES key using his public key and decrypt the file using the AES key.